WireGuard is a modern VPN protocol that is fast and secure and uses public key exchange. When compared to OpenVPN, WireGuard provides much better performance. This article explains creating a WireGuard Site-to-Site VPN tunnel between Vigor Routers.
1. On the VPN server, create a WireGuard VPN LAN to LAN profile: Go to VPN and Remote Access >> LAN to LAN, click on an available index to edit the profile.
2. Edit the profile as follows:

The WireGuard Settings window will pop up after selecting WireGuard.


3. On the VPN client, create a WireGuard VPN LAN to LAN profile: Go to VPN and Remote Access >> LAN to LAN, click on an available index to edit the profile.


4. Go to the VPN Server’s WireGuard VPN Settings page again and paste the VPN Client’s Public Key. Click X or OK to exit the window then click OK to save the setting.

5. On the VPN client router, go to VPN and Remote Access >> Connection Management, select the WireGuard VPN profile and click Dial to activate the tunnel.

We may ping a remote IP to check if the traffic over WireGuard VPN works.

Note: If the Wireguard LAN to LAN VPN is up, but the ping to remote network doesn't work, we can check if the Interface IP is conflicted with the remote VPN network via VPN and Remote Access >> WireGuard. The interface IP is an IP for the Wireguard interface, and it can be any IP as long as it is not conflicted with a network IP. We recommend using the router's LAN IP as the Interface IP. Click Generate a Key Pair, change the Interface IP, and click OK to save it.

When using WireGuard VPN in NAT mode
We only need to add the settings below for creating the WireGuard VPN in NAT mode.
1. On the VPN server, enter the IP that will assign to the VPN client in the Client IP Address field.

2. On the VPN client, enter the IP that the server gives in the IP Address field.

3. On the VPN client, select NAT for the Mode in the TCP/IP Network settings.

WireGuard VPN between Vigor2136s
To configure the WireGuard VPN between two Vigor2136s easily, please open both routers’ Web pages simultaneously.
1. Set up the General Key on the WireGuard VPN Server
Activate WireGuard VPN service via VPN/ General Setup/ WireGuard
Default Key Pairs Setting
Click Generate to generate the Private Key.
The Key Pairs in the General Setup are for the Vigor Router. The peer WireGuard VPN clients need the Vigor Router’s Public Key to create the WireGuard VPN profile. Copy the Public Key of the WireGuard VPN server.
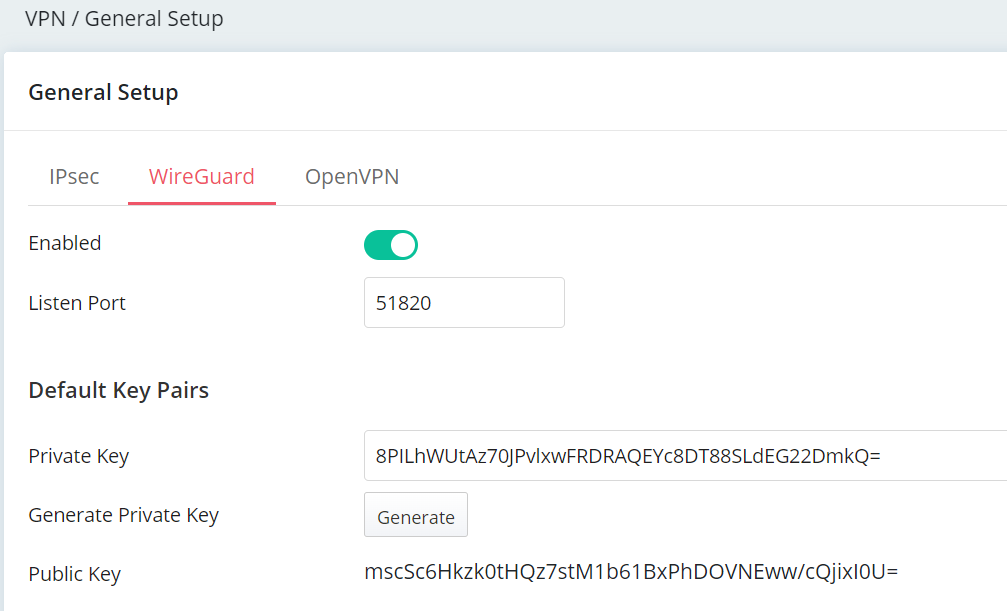
Listen on Interface Settings
This setting specifies which WAN will accept VPN connections. Options are All Interfaces or Specified Interface.
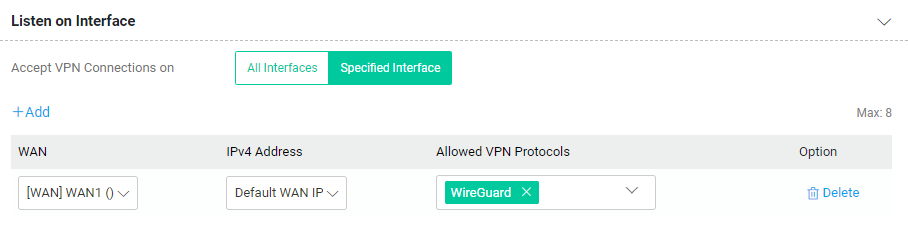
VPN Access List Setting
Select the required VPN access control mode. By default, the Vigor router allows all IP connections. To allow or disallow specific IP addresses, use the Block List mode or Allow List mode.
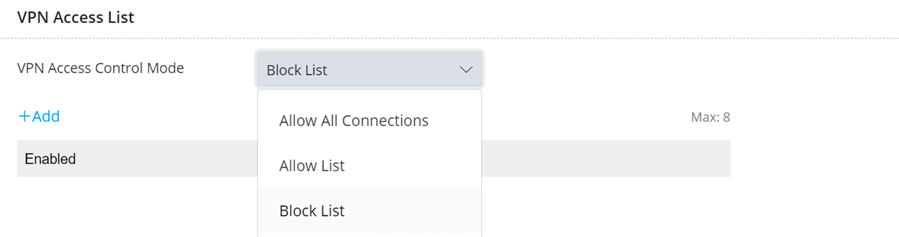
Brute Force Protection Settings
Specify the maximum number of failed VPN login attempts and the period for blocking access after reaching the threshold.
2. Set up the WireGuard VPN Site to Site Profile on the VPN Client Router
Go to VPN / Site to Site VPN, click Add + to create a VPN Site to Site Profile.
2.1 In General Settings:
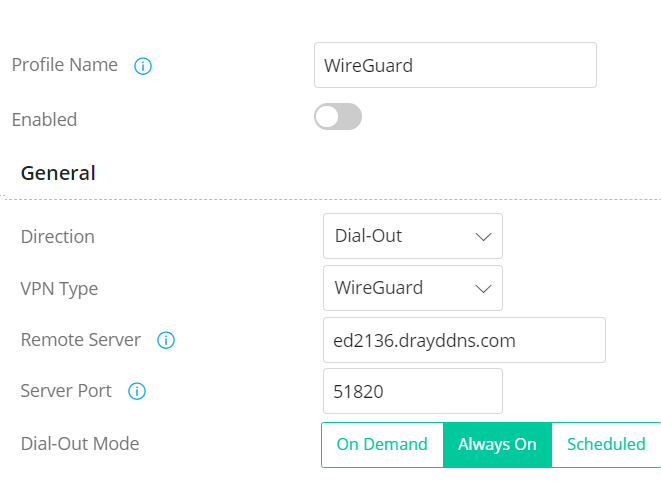
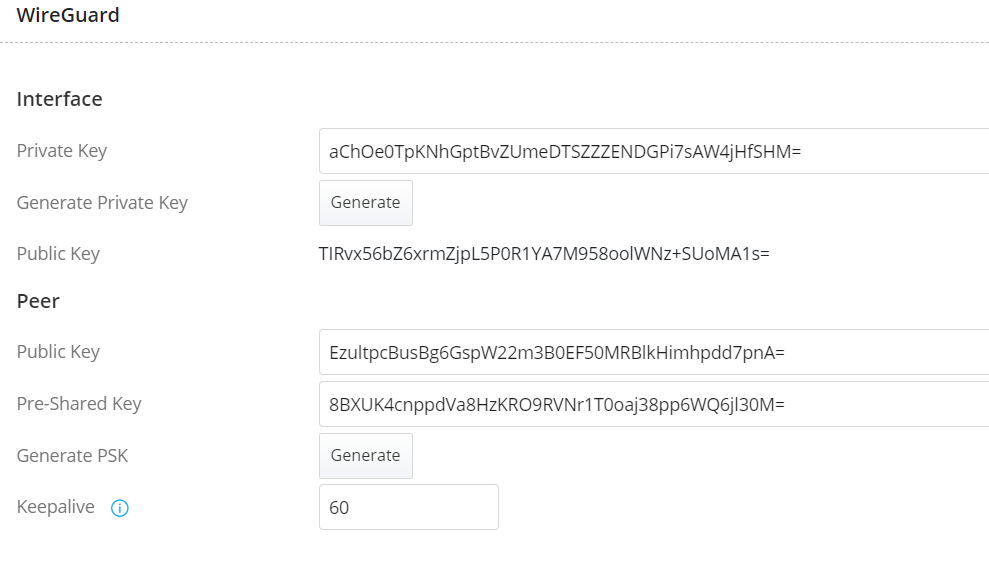
2.2 In WireGuard Settings
Interface
Peer
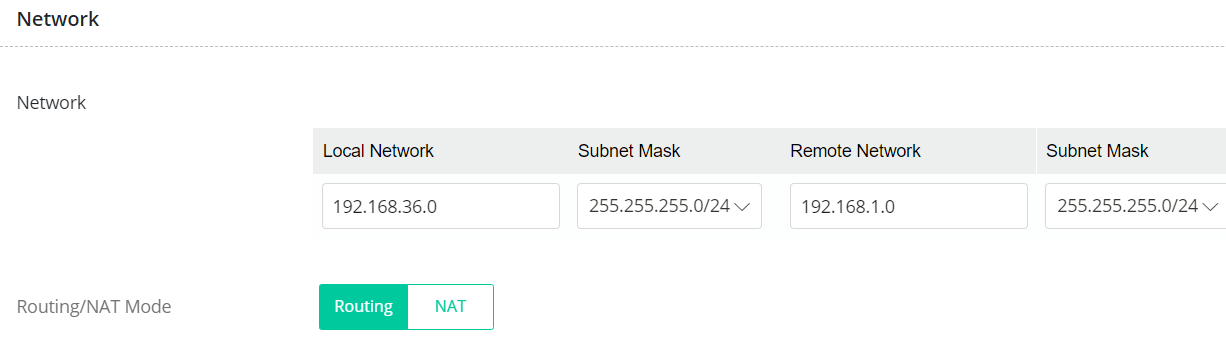
2.3 In Network Settings
3. Set up the WireGuard VPN Site to Site Profile on the VPN Server
Go to VPN / Site to Site VPN, click Add + to create a VPN Site to Site Profile.
3.1 In General Settings:
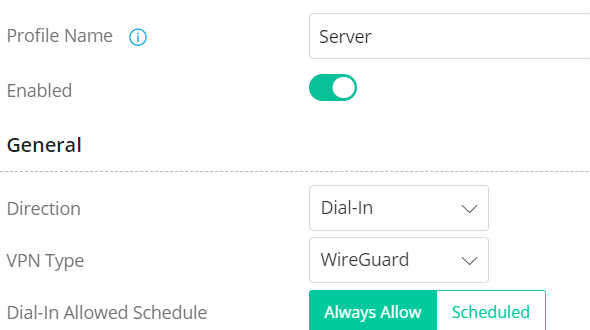
3.2 In WireGuard Settings
Peer
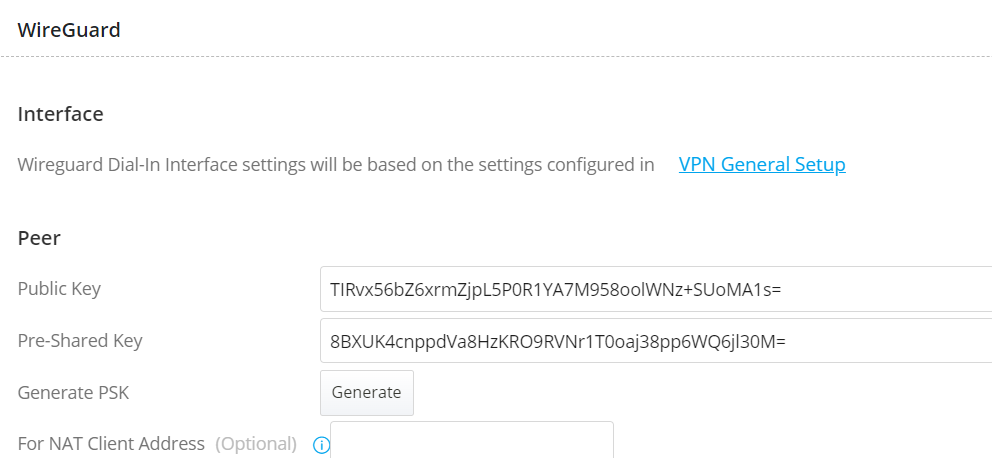
3.3 In Network Settings
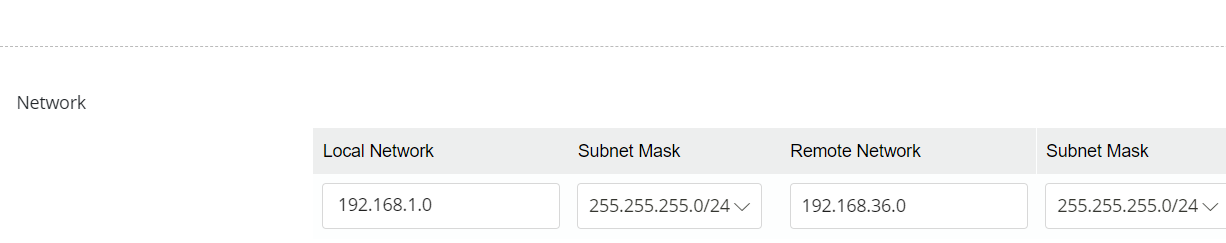
4.Go back to the Client Router’s VPN Site to Site Profile Setup page and Apply the settings.
5. Go to VPN / VPN Connection Status to check if the WireGuard Site-to-Site VPN connection is established.
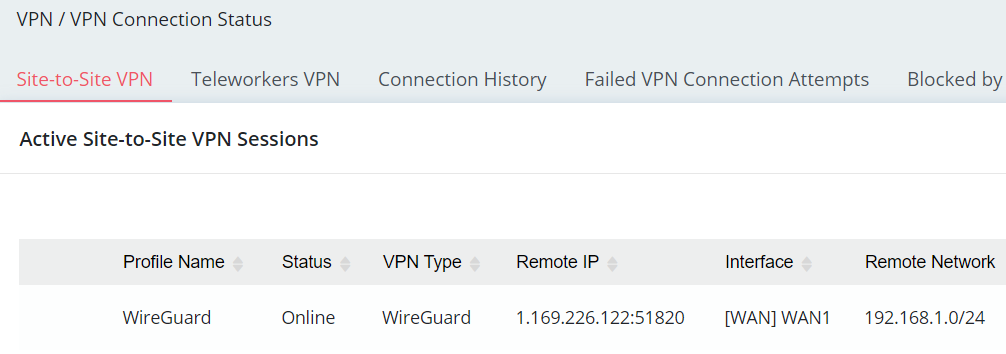
And use ping to ensure if the connection to a remote Server through the VPN works.
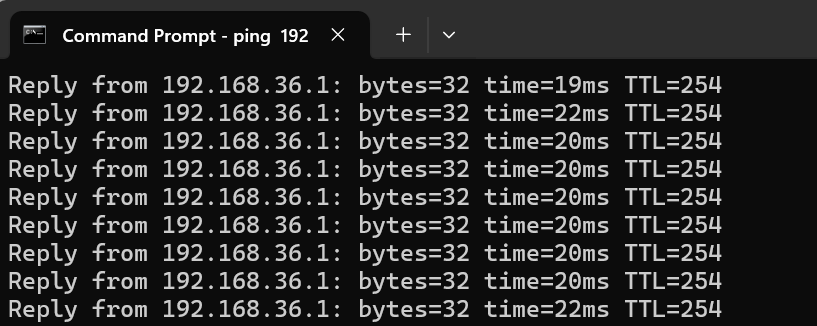
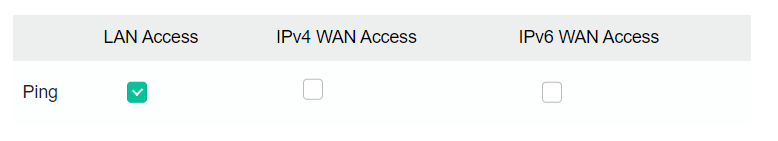
When pinging the remote router’s LAN IP to check the connectivity, please enable the Ping for LAN Access option via System Maintenance / Management. Then, the remote router can reply to Ping over the VPN connection.
Published On: 2022-01-21
Was this helpful?
