Identity and Access Management (IAM) is a framework of policies designed to meet cyber security requirements by managing how users interact with digital resources
and controlling their permitted actions. This feature is now available in DrayOS 5 Routers, offering a new approach to network management. This article will
demonstrate how to use IAM on DrayOS 5 Router.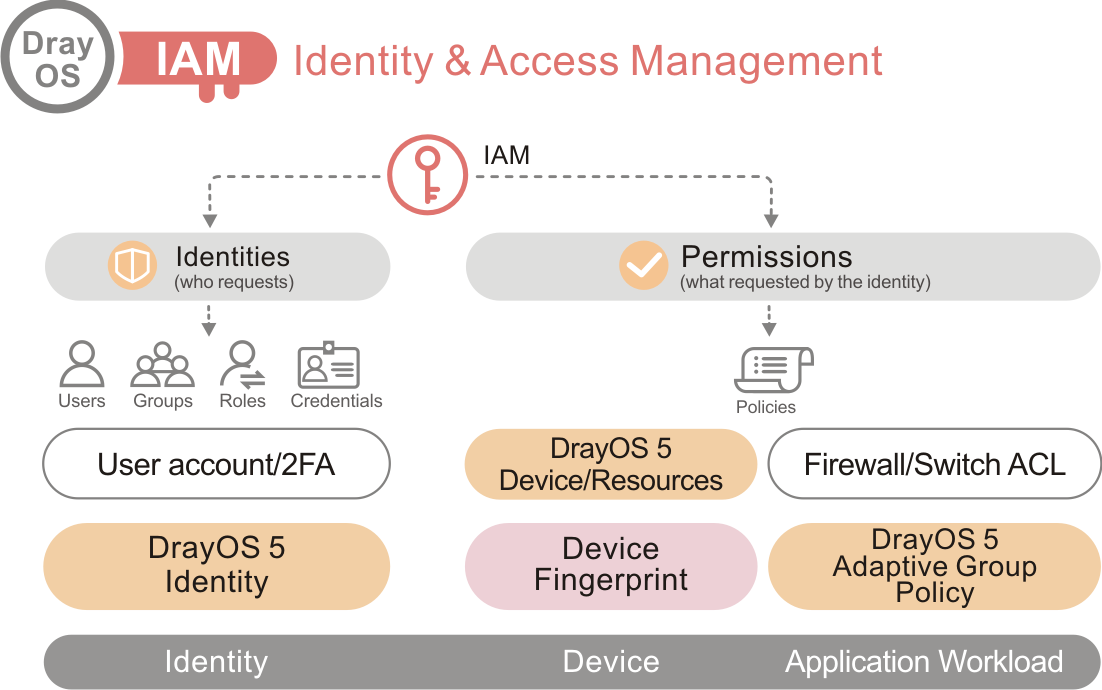
IAM offers a comprehensive set of powerful security enhancements for DrayOS 5 routers. With IAM, administrators gain the ability to control user privileges, define access policies, and seamlessly coordinate group policies with the firewall and conditional access settings. Compare to the legacy firewall on DrayOS 4 routers, IAM allows administrators to manage the network base on roles. The Users & Groups option allows administrators to assign different levels of privileges to user accounts.
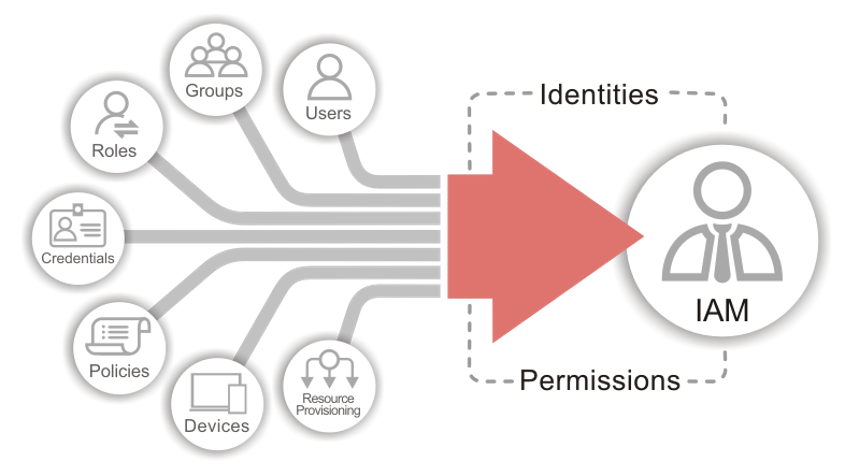
Also, DrayOS5 is Zero Trust ready! The spirit of IAM is never trust, always verify. Under IAM policies you’ll find access policies, group policies and conditional access policies.
Access policies ensure that only authorized users or devices can access resources and services such as, users by login or guest hotspot and devices by MAC address list.
Group policies combines IP & Content filters as well as the conditional access settings.
Conditional access policies can require users to provide multiple forms of authentication before they are granted access to a resource. Policies can also be applied to VLANs.
The Resources option allows recording IP and MAC addresses of local devices like workstations, servers, etc., which can also greatly enhance the effectiveness of your access policies.
Configuration Example
The following example will show how to allow privileged LAN users to access Internal server resource.
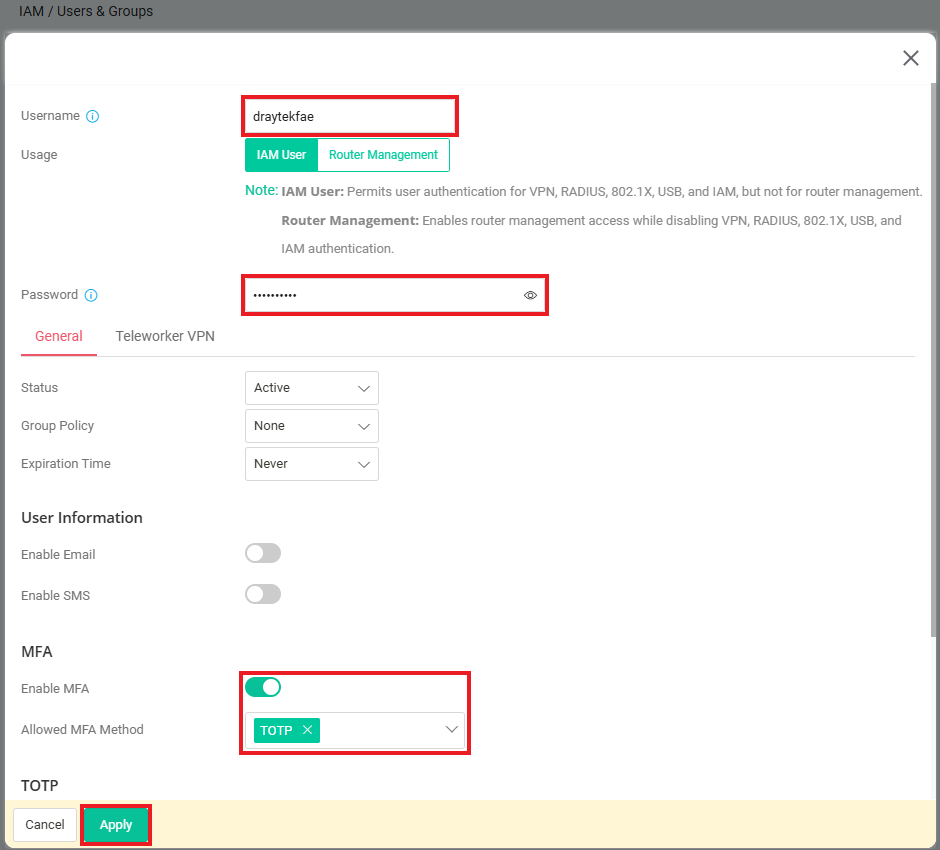
- Go to IAM / Users & Groups / Users page, click “Add” button to create IAM user profile as follows:
- Enter Username and Password.
-
Enable MFA with TOTP.
-
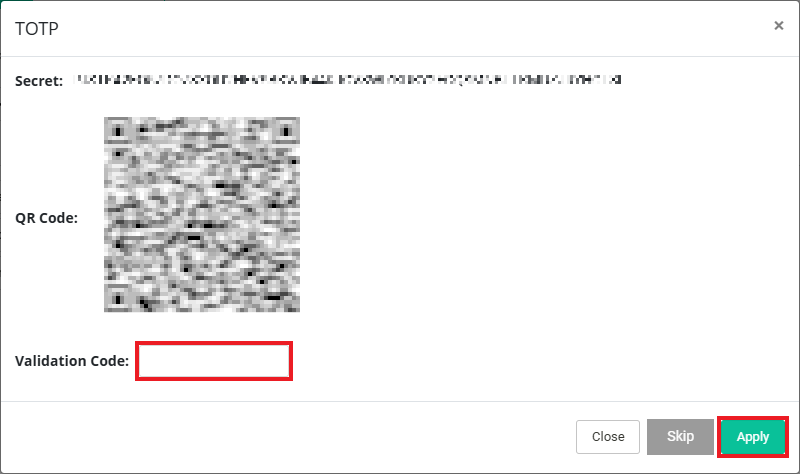
Click Apply and validate the TOTP token with Authenticator app.
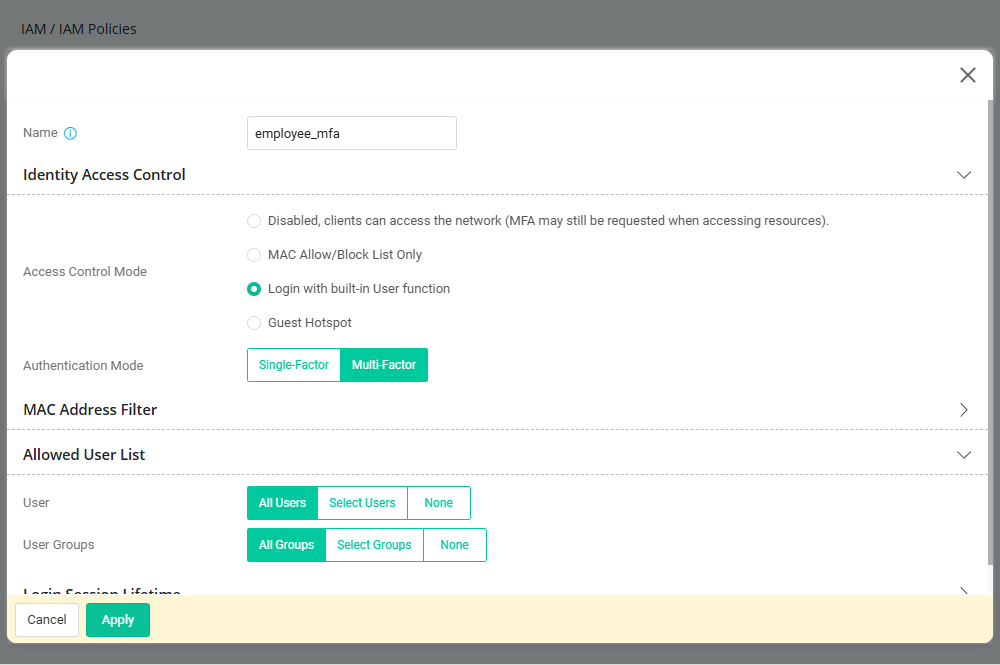
- Go to IAM / IAM Policies / Access Policies page, click “Add” button to create Access Policy profile as follows:
- Enter the Name of the policy profile.
- Select Login with built-in User function in Access Control Mode.
- Select Multi-Factor in Authentication Mode.
-
Click "Apply” to save the profile.
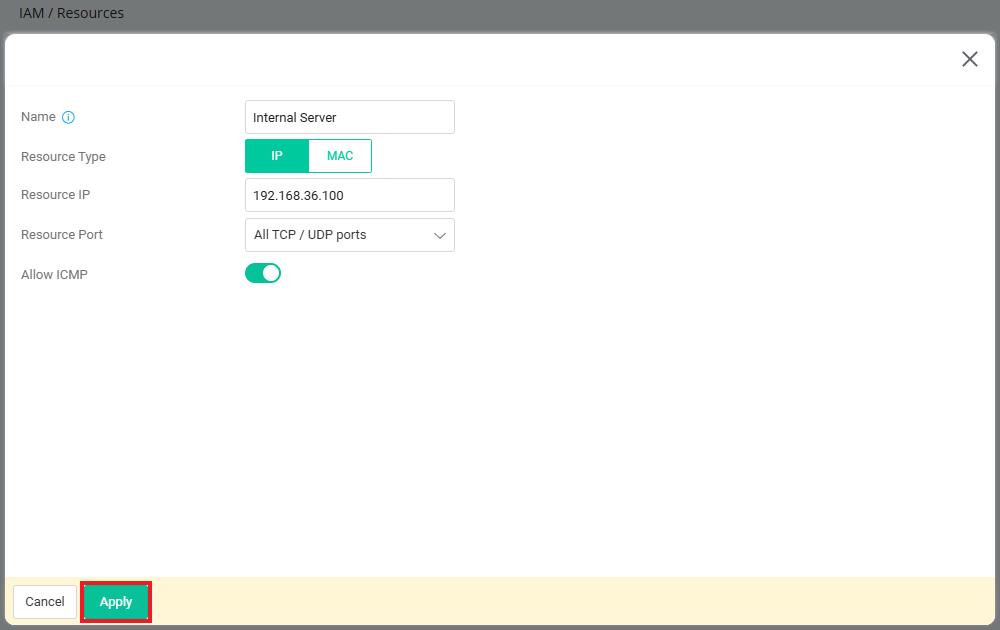
- Go to IAM / Resources page, click "Add" button to create Resource as follows:
- You can choose the resource Type and enter the Address according to your environment.
- Here we use an ACS3 server, IP Address: 192.168.36.100 as example.
-
Click "Apply" to save the profile.
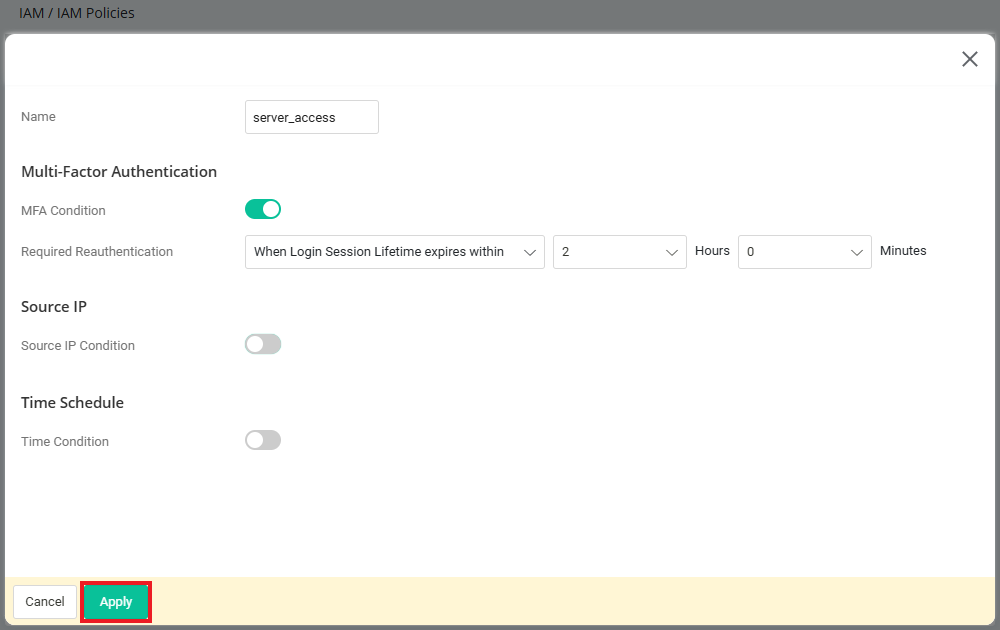
- Go to IAM / IAM Policies / Conditional Access Policy page, click "Add" button to create conditional access policy profile as follows:
- Enter the Name of the policy profile.
- Enable MFA condition to request MFA when accessing resources.
-
It’s optional to setup Source IP and Time Schedule to allow user’s access from specific IP and time.
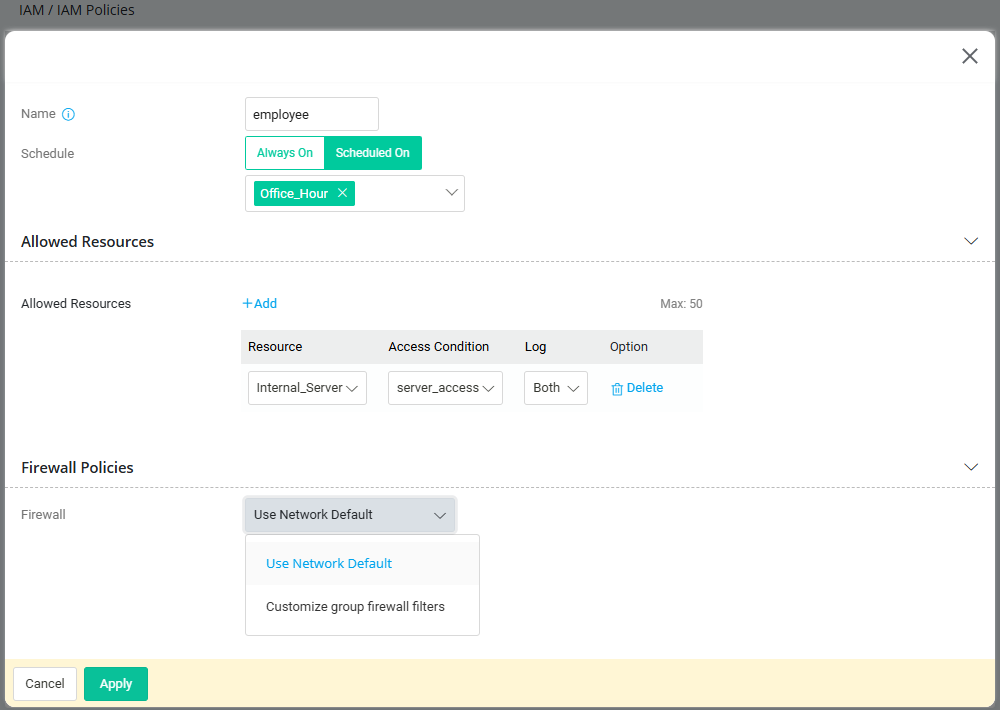
- Go to IAM / IAM Policies / Group Policies page, click “Add” button to create group policy profile as follows:
- Enter the Name of the policy profile.
- Enable time schedule to restrict the access during office hour.
- Apply resource & conditional access policy in Allowed Resource.
-
It’s optional to setup customized group firewall filter to restrict user's Internet access.
-
Go to IAM / IAM Policies / Apply Policies to LAN page, apply access policy profile and group policy profile to LAN2.
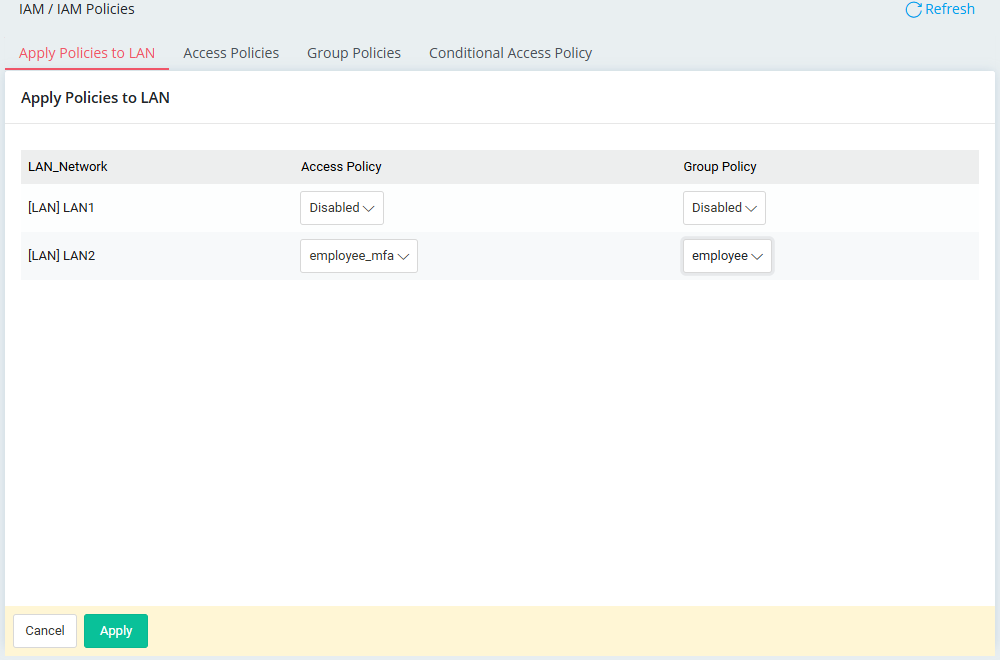
-
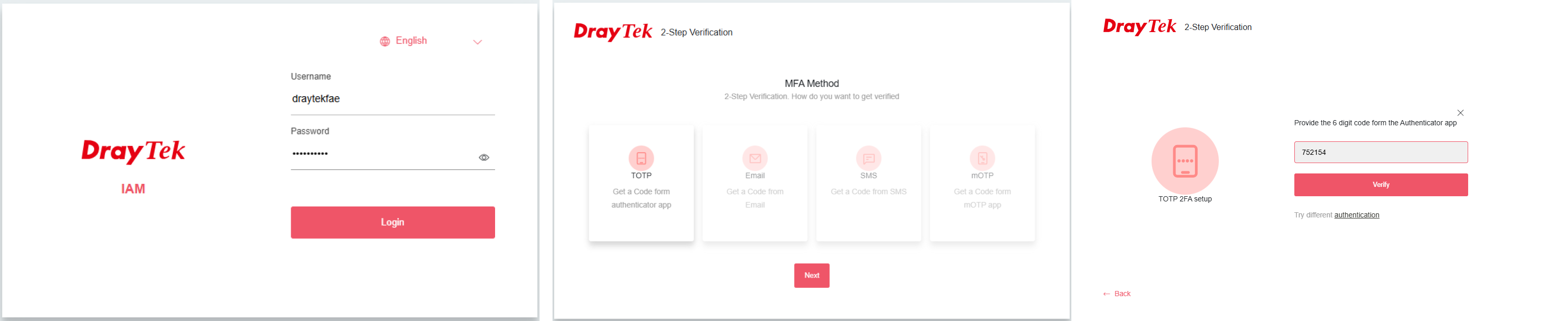
Privileged users are now required to log in with 2FA to access the internal server.
Published On:2024-11-14
Was this helpful?
