This article introduces how the firewall works in DrayTek DrayOS 5 routers, such as the Vigor2136. We will look at two scenarios for reference.
The Vigor2136 has three filters in the Firewall Filters setup menu. These are IP Filters, Content Filters, and Default Filters. IP Filters and Content Filters are independent. Therefore, the received packets will be checked in the following sequence:
1. IP Filter rules
2. Content Filter rules
3. IP Filters Default Action (when there is no IP Filter and Content Filter rule matched)
4. Content Filters Default Action (apply the default content filter action if matched. If not, do the opposite action of default content filter. See Filter Actions below.)
This means that packets are first inspected by the IP Filters and then inspected by the Content Filters before the IP Filter rule passes them or when no IP Filter rule matches. Finally, the Default Filters act when the packets do not match the IP or Content Filter rules.
Below is a flowchart of how the filter works on outgoing packets.

IP Filters: Checks data packets source and destination IP addresses, protocol, and service (port number).
Content Filters: These include APPE, URL Filter, and WCF. APPE is filtered by a defined pattern. URL and WCF Filters filter servers to connect to by checking the domain name in the DNS query packet or SNI (Server Name Indication) in the TLS Client Hello packet.
Default Filters: Checks packets that do not match IP and content filter rules.
Filter Actions
IP Filters
- Pass - Pass the packet immediately if there is no matching Content Filter rule.
- Block - Discard the packet immediately; no other filter rules will apply.
Content Filters
- Pass - Pass the packet immediately; no other filter rules will apply.
- Block - Discard the packet immediately; no other filter rules will apply.
IP Filter Default Action
- Pass - Pass the packet immediately if Content Filter Default Rule is disabled.
- Block - Discard the packet immediately; no other filter rules will apply.
Content Filter Default Action
- Pass - Pass the packet matched only and discard the packet not matched.
- Block - Discard the packet matched only and pass the packet not matched.
Force DNS Redirection
By default, Force DNS Redirection is enabled in each LAN profile. All outgoing DNS lookups will be redirected to the router's LAN IP to improve the domain lookup performance by caching DNS queries and results.
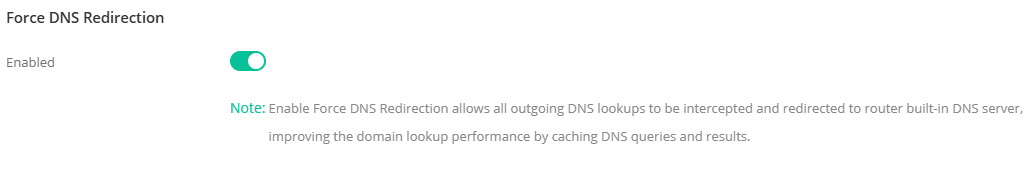
When this option is enabled, or clients use the router as the DNS server, the DNS traffic will be treated as LAN -> Localhost. The IP Filter rules will ignore this DNS traffic and continue to the inspection by Content Filters.
Below is a flowchart of a DNS packet when Force DNS Redirection is enabled.

Scenario 1. Blacklist. Pass more by default (IP Filters Default Action Pass) but block a few exceptions
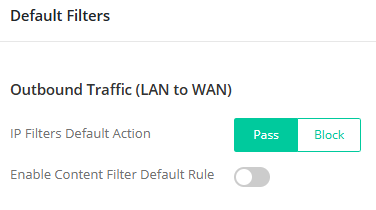
In a simple-use network where only certain specified content needs to be restricted (such as home or school), it is recommended to leave the IP Filter Default Action at Pass and only block specific IPs and content.
For example, in a teaching institution, network requirements are:
- All teachers and students can access the Internet but are restricted from Adult content.
- Prevent students from streaming media and games.
We can enable the Content Filter Default Rule to block all people from accessing adult content.
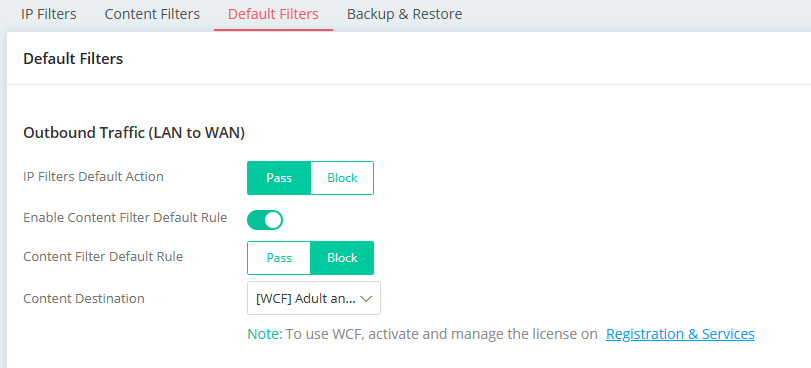
Then, a content filter rule will be set to block streaming media and games for all students.
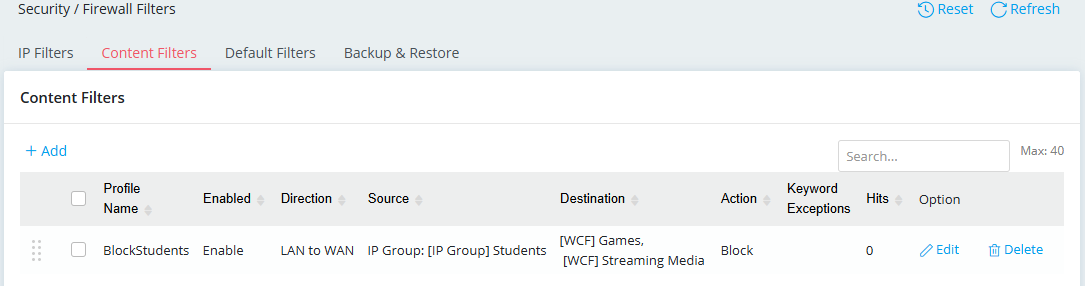
Scenario 2. Whitelist. Block more by default (IP Filters Default Action Block) but pass a few exceptions

For restricted networks with higher security requirements (such as banks or IT Companies), setting the IP Filter Default Action to Block is recommended. The firewall only allows access to specified Servers (IPs) and contents.
Take a company network as an example; each department in the company has different firewall policies; for example,
- The support team can use Anydesk and view news sites, while the marketing and sales department can only view news sites.
- The support team can access the external web server.
Set a Content Filter rule for the support team to use Anydesk. Set the other Content Filter rule for the support and sales teams to enable viewing news sites.
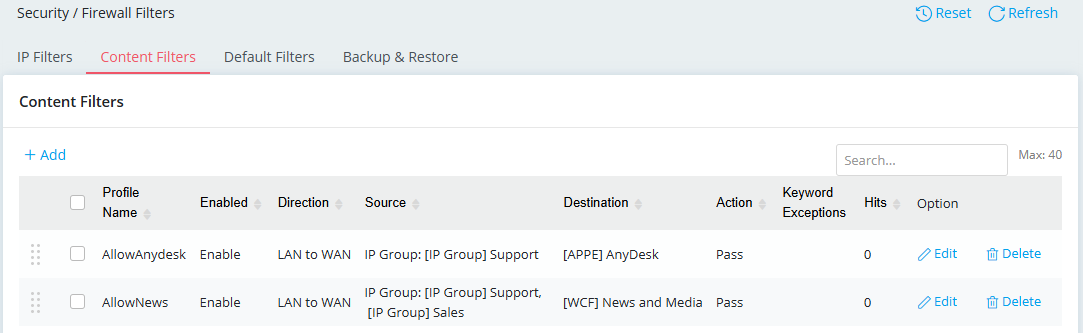
Set an IP Filter rule to allow the support team to access the web server on the Internet.

Published On:2025-01-07
Was this helpful?
