On the Vigor Router, each WAN interface has a DMZ (demilitarized zone), where you can add a LAN host (IP address) and make it completely exposed to the Internet. The DMZ host will be accessible by the IP address of the WAN interface, and the router will map all the unsolicited traffic on the WAN interface to it. It is the solution when you need to do forward traffic to a LAN server but cannot define the traffic by UDP or TCP ports.
To add a host into DMZ, go to NAT >> DMZ Host, and go the tab of the WAN interface you want the host to be accessed from
- For WAN 1, select "Private IP"; For other WANs, check Enable.
- Click Choose IP at Private IP and select the IP address of the DMZ host
- Click OK to apply the settings.
Note that the following functions have higher priority than the DMZ Host settings so that traffic will not be forwarded to the DMZ host if: (1) It matches the Port Redirection settings. (2) It matches the Open Ports setting. (3) It is destined to the ports on which the router itself is actively listening. (For example, if WAN management is enabled on the router and allows telnet and HTTP access, inbound packets to ports 23 and 80 will be intercepted by the router).
Set up Access Control List (Optional)
Instead of anyone could access DMZ, we may prefer to set up a whitelist for the source IP. We can achieve this by two firewall rules. Go to Firewall >> Filter Setup >> Default Data Filter to add the rules:
Rule #1 (usually we start adding rules from index 2)
- Direction: WAN -> LAN/DMZ/RT/VPN
- Source IP/Country: Allowed source
- Destination IP/Country: DMZ host
- Action: Pass Immediately
Rule #2
- Direction: WAN -> LAN/DMZ/RT/VPN
- Source IP/Country: Any
- Destination IP/Country: DMZ host
- Action: Block Immediately
Now, only source IP 111.111.111.111 could access DMZ host 192.168.1.11
Before the configuration, please note that Port Forwarding and DMZ Host have higher priority than the router's local service in the DrayOS5 platform.
For example, if we enable a DMZ host for WAN1, remote management of the router (e.g., HTTP and Telnet) will not work from WAN1.
The order of Priority:
Port Forwarding -> DMZ Host -> Port Trigger -> Local service.
Set up DMZ Host
1. Go Configuration / NAT / DMZ Host. Click +Add to add a DMZ host and configure it as follows.
- Check Enabled.
- Select the WAN interface and WAN IP address you want the host to be accessed from.
- Enter the IP address of the DMZ host.
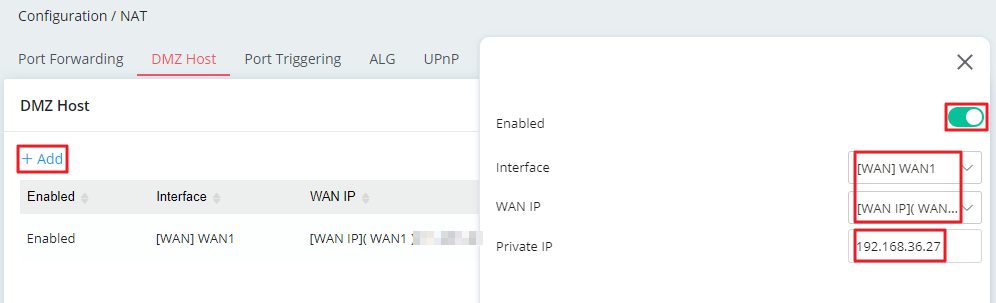
Then click Apply to save the setting.
Set up Access Control List (Recommended)
Instead of anyone accessing DMZ, we may prefer to set up a whitelist for the source IP. We can achieve this by two firewall rules.
Go to Security / Firewall Filters / IP Filters to add the following rules.
One is to allow specified source IPs to access the DMZ host, the other is to block the access from any resources.
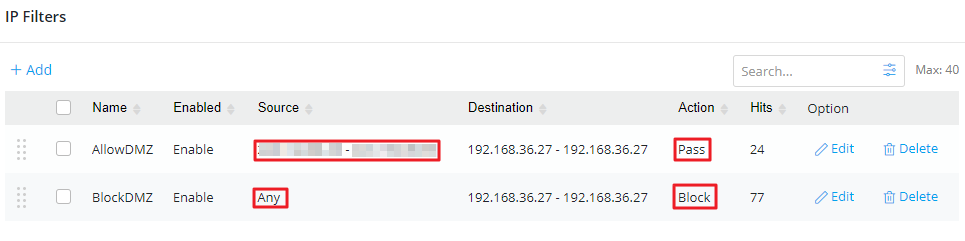
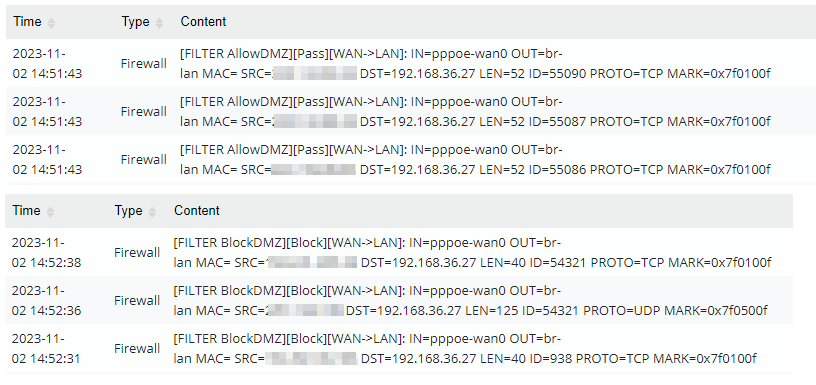
After finishing the setup, only specified source IPs can access DMZ host 192.168.36.27. We can monitor in the syslog.
To add a host into DMZ, go to NAT >> DMZ Host, and add a profile as follows:
- Select the WAN interface where the LAN host should be accessed for WAN Profile
- Enter the IP address of DMZ Host IP at DMZ Host IP
- Click Apply to apply the settings.

Note that the following functions have higher priority than the DMZ Host settings so that traffic will not be forwarded to the DMZ host if:
(1) It matches the Port Redirection settings.
(2) It matches the Open Ports setting.
(3) It is destined to the ports on which the router itself is actively listening. (For example, if WAN management is enabled on the router and allows telnet and HTTP access, inbound packets to ports 23 and 80 will be intercepted by the router).

Published On: 2018-05-09
Was this helpful?
